Every blockchain has a few invisible forces moving behind the scenes. Some are good, some are harmful. And one of the most misunderstood forces is MEV (Maximum Extractable Value), a term that simply describes the extra value that bots extract by manipulating the order of transactions in a block.
If you trade $TAO or any Bittensor-related token, you have probably seen sudden price spikes right before your buy or strange dips right after. That is usually not random, it is MEV.
The good news is that you do not need deep technical expertise to understand it and you definitely do not need to be an expert to defend yourself (at least, not in Bittensor!)
Let’s explore MEV in a simple way as well as the tools built for Bittensor traders to avoid being targeted.
What MEV Really is
MEV is the profit that bots make by reordering transactions inside a block.
When you send a trade on a decentralized exchange, it enters a public waiting room called the mempool. Bots watch this waiting room every second, looking for large trades (buys or sells). The moment they notice a big order that can move the price, they jump in front of it, move the market, and then trade again behind it.
This process is called a sandwich attack.
It is not personal, it’s simply automated profit hunting. For traders, the result feels the same: worse prices.
Traders in the Bittensor ecosystem might experience this often because subnet “$ALPHA” tokens sometimes have low liquidity.
A single buy can shift the price by several percent. This is exactly the kind of movement bots love.
How Sandwich Attacks Actually Work
A sandwich attack follows three predictable steps.
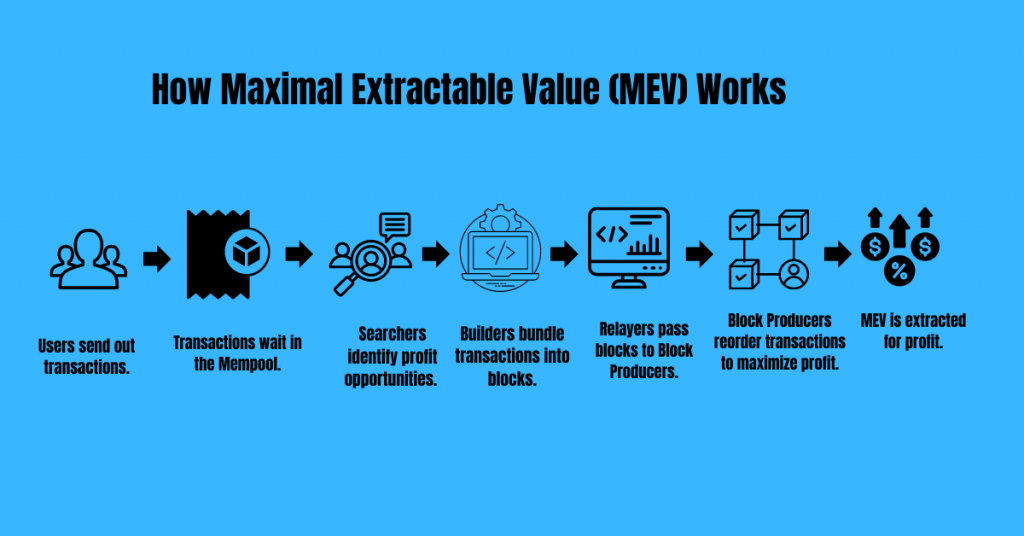
a. The bot sees your large buy in the public mempool.
b. It submits its own buy first, pushing the price up before your order goes through.
c. After your trade fills at the higher price, the bot immediately sells back to the pool and takes the profit.
It happens this same way for the “sells” too.
Everything happens within seconds. Traders always pay more in this scenario and the bot walks away with free money.
This is the most common MEV attack on $TAO subnet tokens.
How Traders Can Fight Back
Users cannot stop bots from existing, but they can make their trades unprofitable for them. When a bot sees that a sandwich attack will not make money, it simply ignores that transaction.
Here are the most effective ways to defend trades against this attack:
a. Lower Slippage Tolerance: Small slippage settings give bots no room to push the price around.
b. Use Private Execution Routes such as MEV Protection Tools: These tools hide transactions so the bots cannot see it.
c. Split Large Trades into Smaller Pieces: Tiny trades do not move the price enough for bots to care.
d. Trade During Busy Network Times: Bots pay more for gas and often skip smaller opportunities.
All of these strategies work. But the most practical for $TAO specifically are two simple strategies that regular traders use every day.
Tools That Help TAO Traders Stay Safe
Within the Bittensor community, there are already-made tools built to make MEV protection effortless. They are built specifically for Bittensor-native assets:
a. Neutralteq
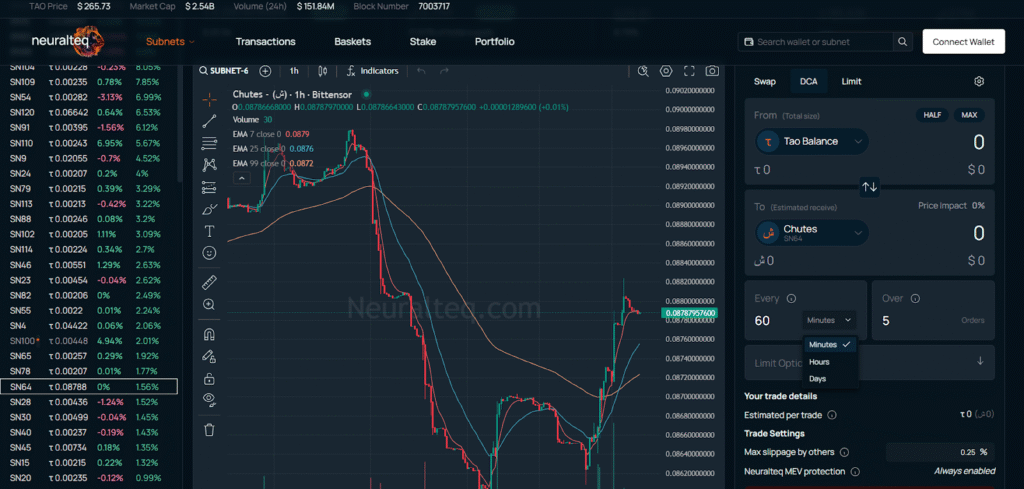
Neutralteq has a “DCA” feature. Standing for Dollar-Cost Averaging, DCA automatically splits trades into small pieces (according to the preset condition set) so that bots cannot sandwich them.
Neuralteq, then, manually buys/sells these small volumes of the assets over time.
This tool is specifically designed for Bittensor subnet “$ALPHA” tokens (since most of them have thin liquidity), one of the simplest options for retail users.
b. TaoApp
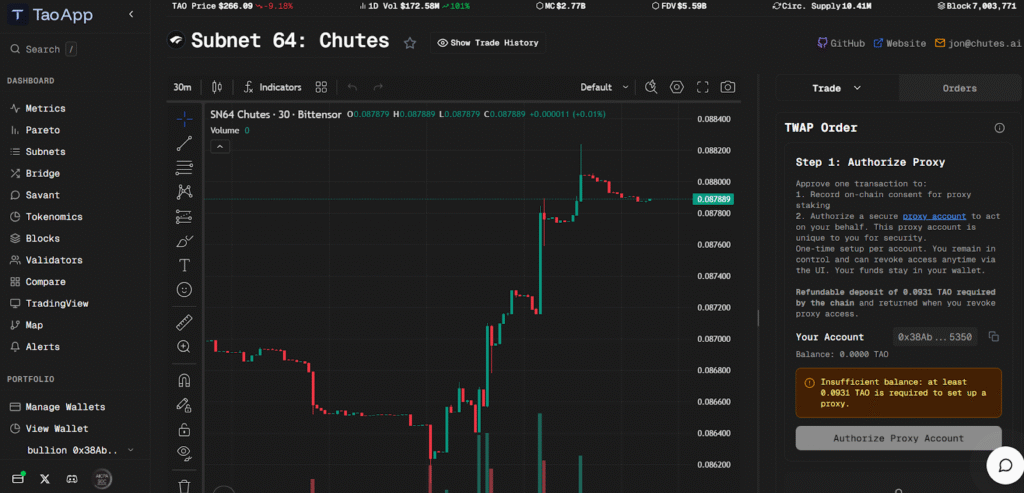
For TaoApp, it has a “TWAP” (Time -Weighted Average Price) feature. This spreads trades evenly over a chosen period of time and keeps each trade small enough that MEV bots lose all incentive to attack.
For example, buys might be processed to a small amount that is purchased at regular intervals. This keeps every trade tiny and invisible to bots.
In real trading, these two methods reduce MEV losses by more than 80% for most TAO traders. They also smoothen out entry prices and reduce emotional decision making.
Both options require almost no technical knowledge and reduces exposure to price manipulation. Also, both solve the core problem without forcing users to use private relays or advanced trading tools.
Final Thoughts
MEV attacks are a natural result of open blockchains. Bots exploit large trades but with the right approach, traders can always turn their trades into something they simply ignore.
Break your orders into smaller pieces using TWAP or DCA. Adopt trusted tools and Bittensor-centric solutions like Neutralteq and TaoApp.
Once you understand how MEV works, protecting trades against them becomes easy. TAO traders do not need to fight bots directly or manually, they only need to make themselves unprofitable targets.
Did we miss any tools for preventing MEV attacks on Bittensor? Share them below.



Be the first to comment