
Bitsec (Subnet 60 on Bittensor) begins with a clear belief that artificial intelligence is transforming code auditing faster than any traditional security firm can adapt. The speed is startling and without the right incentives, code security may struggle to keep up.
Two major developments point to this reality:
a. Artificial intelligence is becoming the new baseline layer of code security across both Web3 and Web2.
b. A new agent-friendly payment system called x402 is emerging, and it allows software agents to pay for services like Bitsec automatically.
Together, they set the stage for a very different future.
Artificial Intelligence Becomes the Default
Across the code auditing world, the most advanced teams are rebuilding their workflows around large language models (LLMs) and autonomous agents.
In Web3:
a. Developers at OpenZeppelin write code while an AI “checks” it in real-time
b. Immunefi hands the first review of bug reports to an artificial intelligence agent
c. Trail of Bits uses machine learning to find issues buried deep in complex codebases
d. Smaller audit firms now rely on artificial intelligence just to decide where to begin.
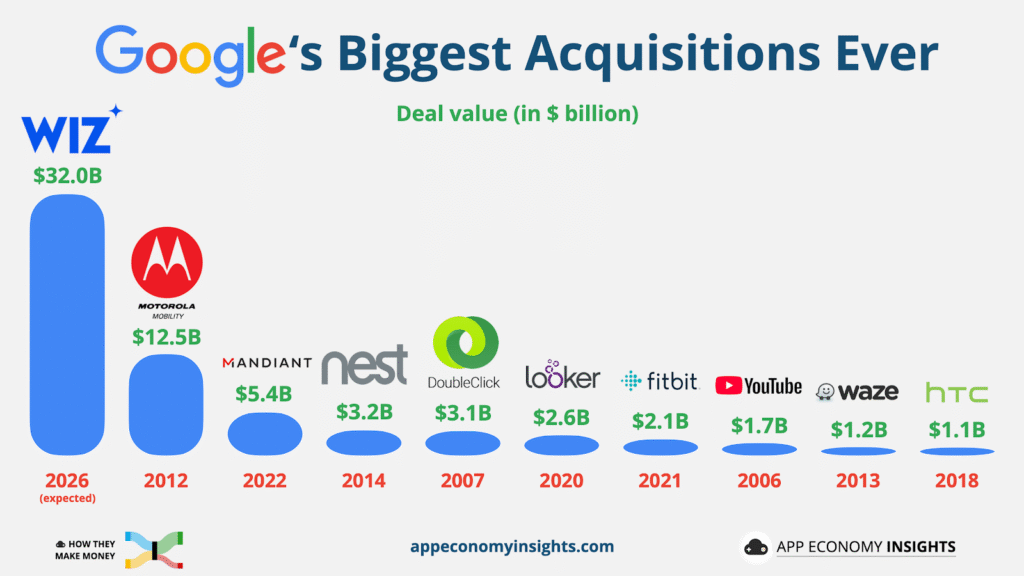
Web2 is undergoing the same evolution at a much larger scale. Companies that cannot build artificial intelligence internally are racing to acquire it.
Recent deals on this include:
a. SentinelOne purchasing Prompt Security for around $250 million dollars
b. Check Point acquiring Lakera for $300 million
c. CrowdStrike buying Onum for $290 million
d. Palo Alto Networks absorbing Protect AI after it purchased SydeLabs for roughly $500 – $700 million
e. Google’s making the biggest move by acquiring Wiz for $32 billion
Artificial intelligence is becoming the standard across the industry. These systems can reason about code, discover hidden vulnerabilities, and make connections that even experienced auditors would miss.
The Limits of Current Tools
Despite the excitement, today’s solutions are still incomplete. They encounter various problems, some of the common and recurrent issues include:
a. Frequent false positives and false negatives
b. Automated fixes that require human intervention
c. Narrow and limited tool scopes
d. New security risks such as prompt injection and agent exploitation
The result is a landscape full of impressive products that still fall short of the fully autonomous future everyone expects.
This creates a clear need for something deeper than better tools. The industry needs new architectures that can absorb new attack vectors, incorporate fresh research, and improve continuously without relying on human capacity.
Why Bitsec Takes a Different Path
Bitsec transforms security into an open and competitive network. Model builders, researchers, and auditors all contribute intelligence that grows over time.
Instead of a static service, Bitsec becomes a living ecosystem that can evolve as fast as the threat environment.
Most importantly, Bitsec is built for a world where software agents, not humans, are the primary consumers of security. That means security cannot depend on tickets, queues, emails, or manual coordination. It needs intelligence that is always available and able to be triggered instantly.
Enter x402 and the Agentic Internet
This is where x402 becomes significant. x402 is a payment system created by Coinbase that allows applications to send stablecoin payments-per-request using standard web protocols.
In simple terms, x402 is becoming the transaction layer of the agent-driven internet. With this, developers can add a single line of code that requires a small-stablecoin payment for an API call, access to compute, a data request, a contract execution or to trigger a security audit (e.g. from Bitsec)
This matters for Bitsec because x402 allows security to become:
a. On demand
b. Automatically paid for
d. Embedded directly into the development lifecycle
Any contract deployment, software update, or agent based action can trigger a Bitsec security check instantly. No scheduling, no waiting in an audit queue and no manual coordination.
Where Bitsec Fits in the New Stack
x402 makes Bitsec accessible across both sides of the emerging internet:
a. For Web3
This is the internet of on-chain systems, smart contracts, and rapid iteration.
What x402 enables:
1. Smart contracts can request security checks automatically
2. Scans can run every time code changes/are updated
3. Developers do not need to pause work for manual reviews
4. Protection becomes continuous rather than reactive
In short, security finally moves at the same speed as crypto development.
b. For Web2
This is the most common internet that consists of traditional apps, APIs, microservices, and SaaS platforms.
With x402:
1. Any API or microservice can request a security scan the same way it requests data or compute
2. Security becomes a simple call rather than a long workflow
3. Artificial intelligence agents can trigger scans automatically without waiting for a human
This makes security feel like a normal part of the infrastructure instead of an isolated step
A New Model for Continuous Security
x402 solves the demand-side problem by enabling seamless access. Bitsec solves the supply-side problem by creating a competitive network that improves continuously.
Together, they create a future where security becomes:
a. Composable
b. Continuous
c. Autonomous
This is a model that traditional audit firms were never designed to support.
The Takeaway
The industry is not simply upgrading tools, it is entering a new architecture. Artificial intelligence is becoming the foundation of security, and autonomous agents are becoming the primary users of that security.
Bitsec and x402 form the core of this new stack. One provides evolving intelligence. The other provides instant access and payment. Combined, they outline what the next era of code security may look like.
A security ecosystem that can keep pace with the internet it protects.




Be the first to comment