
Cover Image Credit: TensorMachina
The internet is entering a dangerous phase. Images can no longer be trusted, videos can no longer be believed and voices can no longer be verified by instinct alone.
What once felt like science fiction has become a daily risk. Deepfakes are no longer novelty experiments or viral curiosities. They are tools of fraud, misinformation, and large-scale manipulation. And they are evolving faster than centralized systems can respond.
BitMind was built for this moment.
The Post-Truth Crisis is Accelerating Faster Than Expected
The scale of the deepfake problem is not theoretical, it is measurable and growing at an alarming rate. In 2023, the number of deepfakes online was estimated at around 500,000 and by 2025, that number is projected to exceed 8 million.
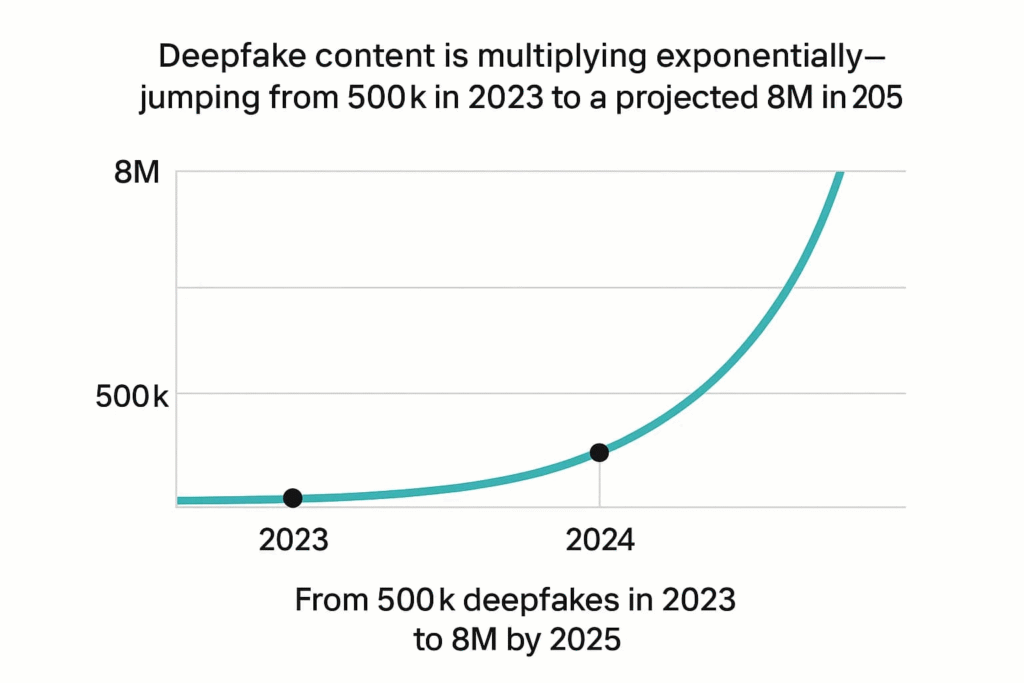
DeepStrike: Deepfake Statistics
This explosion is already producing real-world damage.
A single company reportedly lost over $25 million after an employee was deceived by a deepfake video conference. The executives appeared real, voices sounded authentic, instructions seemed legitimate but none of it was!
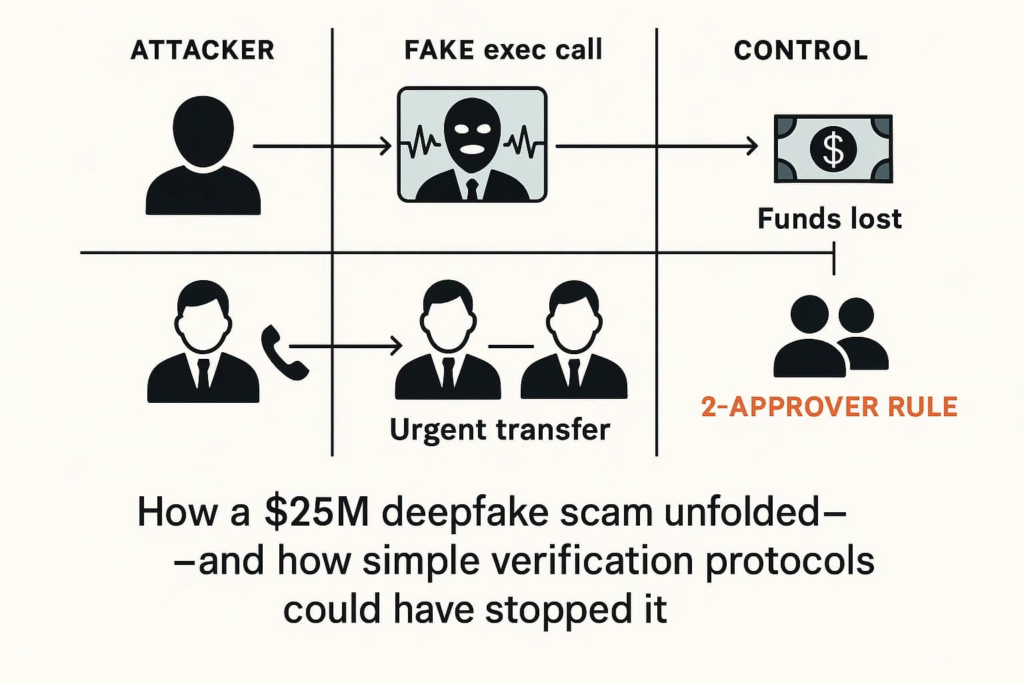
DeepStrike: The $25 Million Scam
The deeper issue is structural: Centralized detection systems rely on static models and slow-update cycles, each new generative breakthrough creates another hole to patch and detection becomes a never-ending game of reaction rather than prevention.
BitMind approaches the problem differently.
BitMind’s Core Insight: You Cannot Fight Adaptive AI With Static Defenses
Deepfake detection fails when it is treated as a finished product rather than a living system. BitMind reframes detection as a continuous adversarial process, where truth is not assumed, but constantly defended.
In the backend, BitMind operates inside the Bittensor network as a decentralized, incentive-driven intelligence system (a subnet). Instead of relying on a single company or closed research team, BitMind coordinates global participants who are financially motivated to outperform each other in detecting synthetic media.
The aim is to empower users to detect deepfakes (receive a verdict as to whether a media is real or AI-generated) by simply uploading media files.
Behind that simplicity sits a highly sophisticated adversarial engine.
From Detection Tool to Digital Immune System
BitMind describes its approach as a digital immune system, not a filter. The system is built around continuous competition between two forces:
a. Generators who attempt to create convincing synthetic media, and
b. Discriminators who attempt to detect and classify that media accurately.
This dynamic mirrors biological immunity where threats evolve, defenses adapt and stagnation is eliminated by design.
Every improvement on one-side forces innovation on the other. The result is not a static detector, but a constantly improving intelligence layer.
Introducing GAS: The Generative Adversarial System Powering BitMind
GAS (General Adversarial System) is the architectural breakthrough that transformed BitMind (Subnet 34). Inspired by Generative Adversarial Networks, GAS takes the adversarial concept and decentralizes it across an incentive aligned network. However, instead of two models competing in isolation, hundreds of independent contributors participate in a shared competitive loop.
What makes GAS fundamentally different is how work is submitted and evaluated: Miners no longer host live endpoints, they simply submit models.
This single design choice eliminates many of the problems that plagued earlier systems, including uptime wars, infrastructure costs, privacy risks, and slot monopolization.
How GAS Works in Practice
The system operates through three primary roles.
BitMind: Subnet 34 Performance Dashboard
a. Discriminative Miners: submit detection models designed to classify media as real or AI generated. They are rewarded purely on accuracy, not hardware power or registration timing.
This lowers barriers to entry and shifts competition toward intelligence rather than infrastructure.
b. Generative Miners: create synthetic media designed to fool the best detectors. Rewards are earned only when outputs pass quality checks and successfully challenge top models.
Their work continuously refreshes the benchmark with new edge cases.
c. Validators: act as referees who assemble balanced datasets, score submissions, enforce fairness, and ensure reproducibility.
Together, these roles form a self sustaining adversarial loop.
Why This Architecture Outperforms Centralized Detection
GAS delivers several structural advantages that centralized systems cannot match, including:
a. Continuous evolution rather than periodic updates,
b. Public, auto evolving benchmarks shared across the ecosystem,
c. No registration races or infrastructure arms races,
d. Full-model privacy through submission based evaluation, and
e. Infinite scaling without exposing enterprise data.
Most importantly, the system produces training data as a byproduct of competition. Generators push realism forward, and discriminators harden against it. The benchmark super-cycle never expires.
The Intelligence Behind the Models
BitMind’s detection models are grounded in active academic research. The foundation model draws from the 2024 CVPR paper on neighborhood pixel relationships, allowing it to identify subtle anomalies introduced by generative processes.
Detection extends across multiple modalities, including images, video, and audio, and the system is designed to handle fully-synthetic, semi-synthetic, and manipulated content such as face swaps and voice cloning.
From Open Competition to Enterprise Deployment
One of GAS’s most important breakthroughs is the clean separation between competition and production. The subnet produces intelligence and delivers it privately.
BitMind: Client-Side Application Interface
Top-performing models are deployed off-chain within BitMind’s controlled infrastructure (or directly inside enterprise environments). Sensitive media never touches the open network.
This enables:
a. Predictable performance with version pinned models,
b. Auditable upgrade paths,
c. Full compliance with enterprise privacy requirements, and
d. No operational burden for customers.
In effect, Subnet 34 becomes a decentralized research and development engine feeding production-grade detection services.
Positioning in the Deepfake Detection Market
Most solutions today fall into one of two categories.
a. Closed commercial APIs that lack transparency and adapt slowly.
b. Academic models that are impressive but impractical for real world deployment.
BitMind sits between these extremes. Open competition drives innovation, and private hosting ensures reliability and trust. The subnet evolves publicly and results are securely consumed.
Why This Matters Now
The future of digital trust depends on systems that can evolve as fast as deception itself. Static detectors will fail, manual moderation will collapse under scale and closed systems will always lag open-adversarial intelligence.
BitMind’s GAS architecture represents a shift from detection as a product to detection as an ecosystem. With this, truth becomes a service, competition becomes a defense mechanism and decentralization becomes a source of trust.
Final Thought
The battle against synthetic media will not be won by a single company or a single model. It will be won by systems that evolve faster than deception, reward intelligence over infrastructure, and treat truth as a shared public good.
BitMind is not attempting to freeze the deepfake problem in time, it is building a system designed to move faster than the threat itself.
By turning detection into a decentralized adversarial market, GAS ensures that no benchmark expires, no dataset stagnates, and no single organization controls the truth pipeline.
In an era where reality itself is increasingly negotiable, BitMind is betting on a simple principle: Truth should win through competition, not authority.




Be the first to comment